Memories of the DirecTV HU card
A story about a small piece of hacking history - memories of the DirecTV “HU card” and the pirates that hacked the smartcard to watch free satellite TV.

(note: This story was originally posted on Twitter Oct 23, 2018.)
The smartcard used by DirecTV after the “H card” became known by pirates as the “HU” card. This was the third smartcard series for DSS (P3 card - period 3). Sometimes referred to as “the football card” because of the artwork on the back of the card.

Oddly enough, the “football card” was not the one OJ Simpson was busted for pirating. That was the previous generation of smartcard, the “H card”.
By 2001, “HU loader” pirate smartcard programming software hit the market even before the hacked “H card” swap-out was done. Some pirates still used hacked H cards while others were buying new pirate HU cards that would last through the impending complete shutdown of the H card.
For prices in the tens of thousands of dollars, dealers bought HU loaders - slightly modified WildThing glitchers, with new software for the new smartcard. The pirate customer base had grown a lot from the previous hacked cards, so there was plenty of demand for the HU hack.
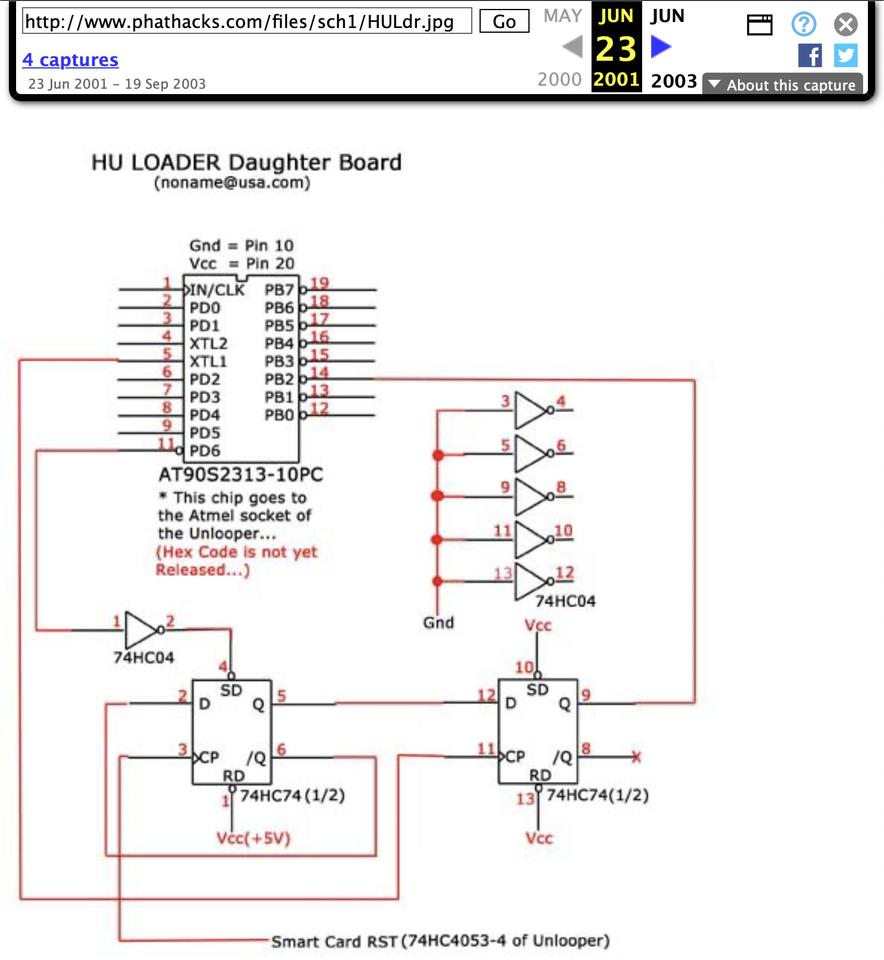
Once the HU loader was in the hands of pirates, it wasn’t long before it was cloned. More sources for HU loaders meant competitive prices. Eventually this led to the secret firmware for the HU loader (the “Atmel code”, for the AT90S2313 chip) being posted on a public website.
After the HU loader Atmel code was posted on the “HackHU” website, anybody with the right kind of smartcard programmer could program their own pirate HU cards. Some pirates modified the WildThing unlooper they bought for the H card to be compatible with the new HU loader.
In the early 2000s, detailed technical information about new hacks, schematics and software, was being spread via the Internet at an accelerated rate. It was no longer a trickle of information from high level dealers filtering down to end users.
A pirate might buy an expensive unlooper or loader, think “I could sell a lot of these”, reverse engineer the PCB and draw a schematic, then a locked chip becomes a dead end. So they post schematics online and hope someone else shares the missing pieces.
Many hardware producers (like Mikobu) competed to build and sell ready-to-use HU loaders. By 2002, for under a hundred dollars anybody could get everything they needed to program pirate smartcards. It was never easier to become a DirecTV pirate, or even a pirate card dealer.

This is another example, a Mikobu III loader/unlooper. The Mikobu III may have been the top selling pirate card programmer in its time, it was considered the “gold standard” to many pirates.
![]()
In 2001, the pirates had to deal with something they recognized all too well by now - their hacked smartcards were looped by a countermeasure against them. A lot of people had gotten used to programming their own smartcards, now they had to hope somebody produced an HU unlooper.
As was typical, the first HU unlooper was in the hands of a commercial pirate, unlooping cards for a fee. Later on, though, things took a turn - the growing mass of hackers chatting and sharing information online led to a new kind of development.
Not just one, but two kinds of HU unlooper were released and shared freely on the internet within days of each other in March 2002. HUFF (to unloop the HU cards responding only FF due to looping) and ul4s (unloop for sure). They both worked great.


By this time there was a kind of “critical mass” of hackers online, developing and sharing hacks for the HU card. Web forums, usually vBulletin or phpBB, were numerous and very active. Pirates helped each other use hacks and searched for new fixes when their cards were shut down.
Popular forums of the time included The Pirates Den (dsschat .com), Interesting Devices (id-discussions), Innermatrix, DR7 .com, Hitec Sat, and dozens others. Many forums were owned by pirate dealers, and some acted as administrators or moderators on others.
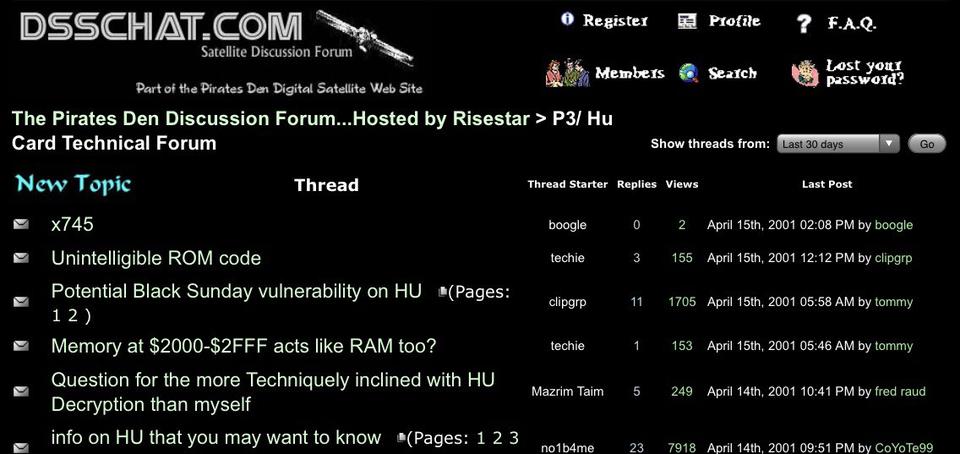
Forums weren’t only for end-user pirates, some of the hackers developing new fixes frequented them also. Over time there was a shift from hacks developed in private and sold through a dealer network, to more widespread, and sometimes free, direct sharing over the Internet.
Some of the hackers became known and respected by many other pirates who admired the skills required to create new and improved hacks. Names like no1b4me, aol6945, and RAM9999 were amongst the elite in the online forums.

Some of these hackers’ names would later show up on a DirecTV website publicizing the many legal actions taken against pirates. DirecTV would proudly boast over 24,000 lawsuits against end users, in addition to action against the hackers and dealers.
Satellite TV piracy was big business. In 1998, Canadian pirate Reggie Scullion (V-Cipher) was raided by police and $4 million in cash, bonds, and bank drafts was seized from his home and business, along with over 10,000 DirecTV smartcards. Pirate business was booming.


By 2003, satellite TV piracy seemed to have been growing out of control for years, despite increasing legal actions against pirates. There were estimates in the press of over 3 million satellite TV pirates, resulting in pay TV companies losing $4 billion in revenue.
Most end-user pirates were paying someone to program, or to unloop, their smartcard. The dealers they paid came in all shapes and sizes - friends, family, small businesses, international pirate dealer networks.
Hackers were writing their own versions of 3M code (or ripping off someone else’s), packaging it up in a loader program with a Windows GUI, or in some cases a script for the popular Winexplorer tool, and offering it for sale.
Pirate software evolved alongside changes in computers and the Internet. From MS-DOS text interfaces to simple Windows applications with two or three buttons, to integrated environments for developing and testing hacks.
For the H card, a software package “BasicH” was been popular for being powerful but also relatively simple to use. Later, with the HU card, even more tools like “ExtremeHU” for programming cards and “HU Sandbox” for developing new pirate code became standard tools for hackers.
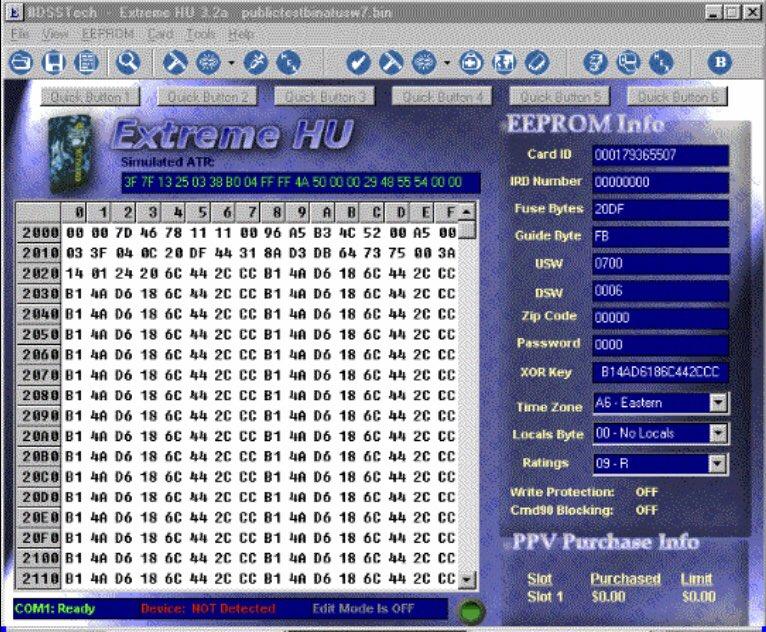
WinExplorer was a widely used tool for smartcard hackers, for writing “.XVB files”, VBScript programs that talked to smartcards or smartcard glitchers. Hackers would share, study, and modify an overwhelming number of .XVB files, a de facto standard for pirate satellite scripts.

Another way used by pirates to watch DirecTV without paying was to use an “emu”, or emulator, system. Using a computer connected to a satellite receiver by a simple PCB interface, the smartcard was emulated to allow all channels to be viewed.
Because hackers hadn’t reverse engineered the HU card ASIC, they could only emulate the microcontroller functions while using a real HU card as an “AUX card”, sending data through the hardware ASIC. The emu software protected the original smartcards from ECMs.
After each version of DirecTV (or later, Dish Network) smartcard was hacked, versions of emulator hacks were developed by pirates. SLE44 and Pitou were H card emulators, Kryptonite an HU emu.

During the era of the pirate HU card, DirecTV may have had a hard time locking out the pirates with glitchers from programming their smartcards, but there was a lot of grief for the pirates in the form of frequent countermeasures shutting down the hacked cards temporarily.
A technique used by the HU card against the pirates was “dynamic code”. Instead of key calculation being done entirely in the ROM and EEPROM firmware known to the hackers, short blocks of program code was sent down in real-time over the satellite.
Dynamic code meant the pirate hackers had to chase a moving target. The code could be changed at any time, and different versions of dynamic code could be rotated in and out of service at any time.
Sending program code over the satellite had been done before, but on the HU card the dynamic code went beyond what pirates had previously dealt with. Let the code run and risk the card being looped. Block unknown code and the card is shut down every few days.
Another electronic countermeasure (ECM) used to target pirate H and HU cards was known as “hashing”. Regions of the smartcard’s memory would be used in the key calculation algorithm, so that the correct decryption keys depended on correct (not hacked) data in the card.
The pirate hackers rose to the challenge, improving their hacks, adding “stealth” and “AI” features to their 3M code. The level of artificial intelligence implemented in these 4 MHz micros with a total 384 bytes of RAM and a KB or two of EEPROM space seems suspect, in retrospect.
Unlike the H card with two chips (microcontroller and ASIC), the HU card only had one chip inside. The HU card had an ASIC on the same silicon die as a Texas Instruments TMS370 microcontroller. 384 bytes of RAM, 16 KB ROM, 8 KB EEPROM.

Another tactic used by DirecTV to shut down pirate cards was to more aggressively target smartcards that were inactive or had been deactivated in their system. The satellite receiver itself could be disabled, instead of relying on software inside the smartcard to disable itself.
The pirates became familiar with the dreaded “Call Ext. 745” messages when their card ID# was disabled - blacklisted by DirecTV. Pirates cloned cards with different ID# or modded the satellite receiver software, and new hacks were developed to bypass the Ext745 shutdowns.
One type of hack was a “no745 board” that acted as a wedge between the satellite receiver and smartcard. The no745 board exploited a bug in the receivers, allowing it to provide the receiver with a fake ID#, to avoid any blacklisting by DirecTV.
Pirates continued to hack the HU card to watch DirecTV for free, though sometimes having to update their pirate card daily, until the HU smartcard was swapped out to a new “P4” card. The P4 card had increased the level of complexity again to be better protected against hackers.
Support for the HU smartcards was disabled permanently by DirecTV in mid-2004. Since then, there has not been a pirate DirecTV hack on the market, or published online. The new P4 smartcards locked the pirates out.

Around that time, a lot of pirates had switched their focus to Dish Network (and Bell Expressvu in Canada), which had been hacked since 1999. That’s another topic with many different stories to be told.
In September 2006 at 27 years old, the hacker behind the HU loader, the first pirate hack for the DirecTV HU smartcard, pled guilty to charges carrying up to 5 years in prison. At the time, he was already serving a 30 month prison sentence for hacking DirecTV Latin America.
In the years since, he and the other hackers involved in DirecTV piracy in the 90s/early 2000s have completed their prison sentences, been released, and put satellite TV piracy in the past.
If this kind of history interests you, think about supporting The Internet Archive - without the Wayback Machine, a lot more hacking history would already have been lost forever.