The pirate business isn't always friendly
The pirate business isn’t always friendly - November 30 1996, RON.EXE released by pirate DirecTV hacker “Fast Eddie” included a rant directed at competing Canadian pirate Ron Ereiser. It was also the first “freeware” hack shared on the internet for DirecTV.
(note: This story was originally posted on Twitter Oct 29, 2018.)
This was a significant release for DirecTV hackers. At the time of RON.EXE, there were not many options available to the public for programming DirecTV smartcards - pirate dealers kept a tight grip on the few hacks developed.
RON.EXE was released during the “F card” DirecTV smartcard era. For many pirates on the internet, it was the first software they could download and use with an inexpensive smartcard programmer to hack DirecTV cards - an alternative to the battery cards.
Occasionally a leaked version of the pirate software used by dealers would surface, but there wasn’t a supply of up to date hacks available for download. So most people had to send their cards to a dealer (or visit a local dealer) whenever they needed updating.
After an electronic countermeasure (ECM), the “3M code” used on pirate smartcards would become obsolete. Since the old 3M code had been targeted, new 3M code had to be developed to bypass the countermeasure and allow the pirate card to continue working.
By this time, the original pirate DirecTV “F card” smartcard programming software developed by Norm Dick - CLONE and 3M - had begun to leak to a wider number of dealers. The “west group” that Ron and Norm were associated with had the original software versions.
Competing pirate dealers had cloned the CLONE software into their own “cl10” program and were selling it. cl10 was followed by other versions, cl12 and cl45.
This put some pirates in a position of having a tool to make clones of smartcards, while competing dealers were selling working 3M hacked cards. Pirates being pirates, the obvious next step was to get a working 3M card and clone it to sell to your own customers.
But sometimes the pirates ran into problems when they tried cloning 3M cards - writing the cloned EEPROM to a smartcard would loop, or 99, it! The smartcard would stop responding to the card programmer, and satellite receivers would no longer recognize it as a valid smartcard.
The problem was that software writing the cloned EEPROM image to the smartcard would write the data sequentially, from beginning to end. But parts of code modified near the beginning of EEPROM required code near the end of EEPROM to have already been changed.
As soon as the programming software rewrote the beginning of EEPROM on the smartcard, the incomplete 3M code would begin to run, before the rest of the 3M code had been written to the smartcard. The result was a looped smartcard - unable to be repaired with the cloning tool!
A straight sequential clone of EEPROM from a working smartcard was all the simple clone software was capable of - so copying a 3M card was out of the question for most pirate dealers at the time, even if they were one of the early few who had bought a pirate smartcard programmer.
Eddie’s release of RON.EXE was a direct shot at Ron’s business programming and selling 3M pirate smartcards. It was an escalation in a feud between two pirate satellite TV dealers, each claiming to offer hacks with better value than the competition.
Both Ron (west group) and Fast Eddie (NorthSat) were established pirate satellite TV dealers in Canada, selling hacked cards locally in their retail stores, and wholesale to other dealers. Both continued to be prominent in satellite TV piracy for years (and smartcards) to come.
The rise of websites and IRC channels focused on satellite TV piracy had accelerated the pirate business and started changing the tone and pace of things from the old days of pirate dealer networks that knew each other personally and stayed connected by phone and dialup BBSs.
Some dealers had started to get access to software to pirate DirecTV, but up to this point the hacks had trickled down through dealers until eventually becoming “leakware”, widely shared over the internet. Now RON.EXE was fully intended to be given away for free online.
Given the content of the message inside RON.EXE, a better term than “freeware” might be “spiteware”. To thousands of pirates online, that distinction didn’t much matter. It was a working 3M hack that could be applied to any DirecTV smartcard with an inexpensive (<$100) device.
Freeware hacks would really take off later during the “H card” and “HU card”, as interest and awareness grew, along with increasing numbers of people connecting online and sharing every tidbit of information they could find.
The original RON.EXE can still be found in an Internet Archive wayback machine copy of Paul Maxwell King’s website. The software could be used with the “MK8” (later 9/10/11/12) smartcard interface sold on the website.
Paul Maxwell King (PMK) ran a business in the UK selling hardware interfaces to pirates. Although PMK didn’t create new hacks, when someone did release pirate smartcard software, PMK would share it on his website, increasing sales of hardware devices like smartcard programmers.


In 1996 there weren’t yet many producers of smartcard programmers suitable for use by satellite TV pirates in North America. The European market had been established earlier than in North America, now providing PMK access to a new market in North America.
Another UK-based hardware developer that became well known in North America was Interesting Devices. The id-discussions .com forum was one of the longest running satellite TV pirate-oriented web sites, kept online until 2015 after Justin passed away.
RON.EXE was surely not the only case of a pirate satellite TV hack released as freeware because of a grudge against another hacker, or as an effort to reduce the commercial value of a dealer’s product. A mix of ego and greed fueled many feuds between pirates - and a lot of hacks.
An afterthought:
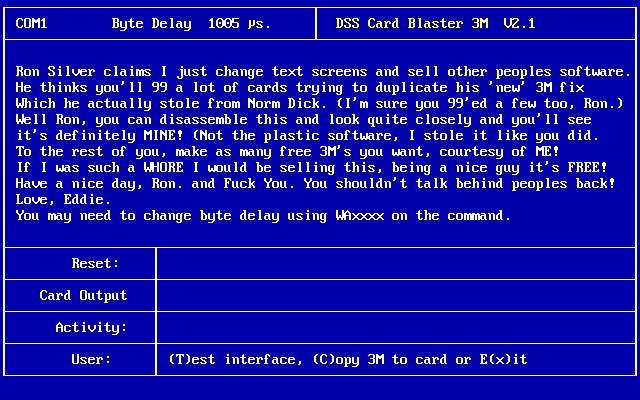
How great was that user interface, MS-DOS circa 1996. One screen (50% rant). Press ‘C’ on the keyboard. That’s it - your DirecTV smartcard “F card” is now hacked and will decrypt every channel.
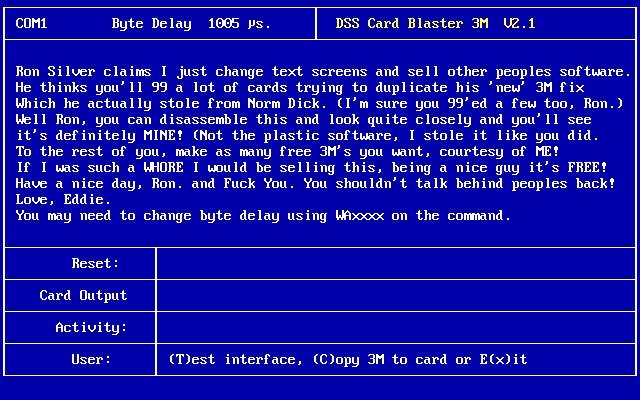
And how is that for a classic angry hacker rant - “Have a nice day, and Fuck You ... You may need to change byte delay using WAxxxx ...”
I’m super pissed off, but also it’s important that my software works properly on your computer - allow me to offer some technical advice.